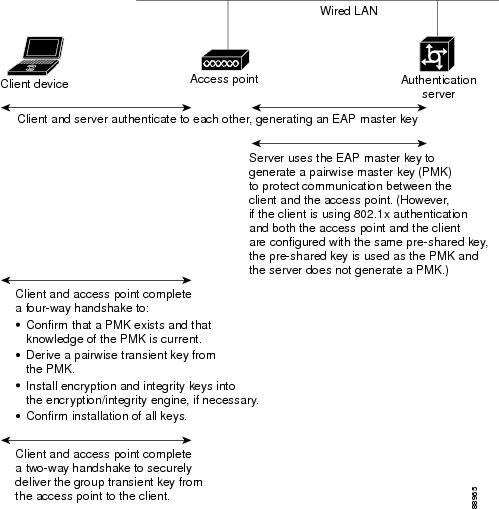
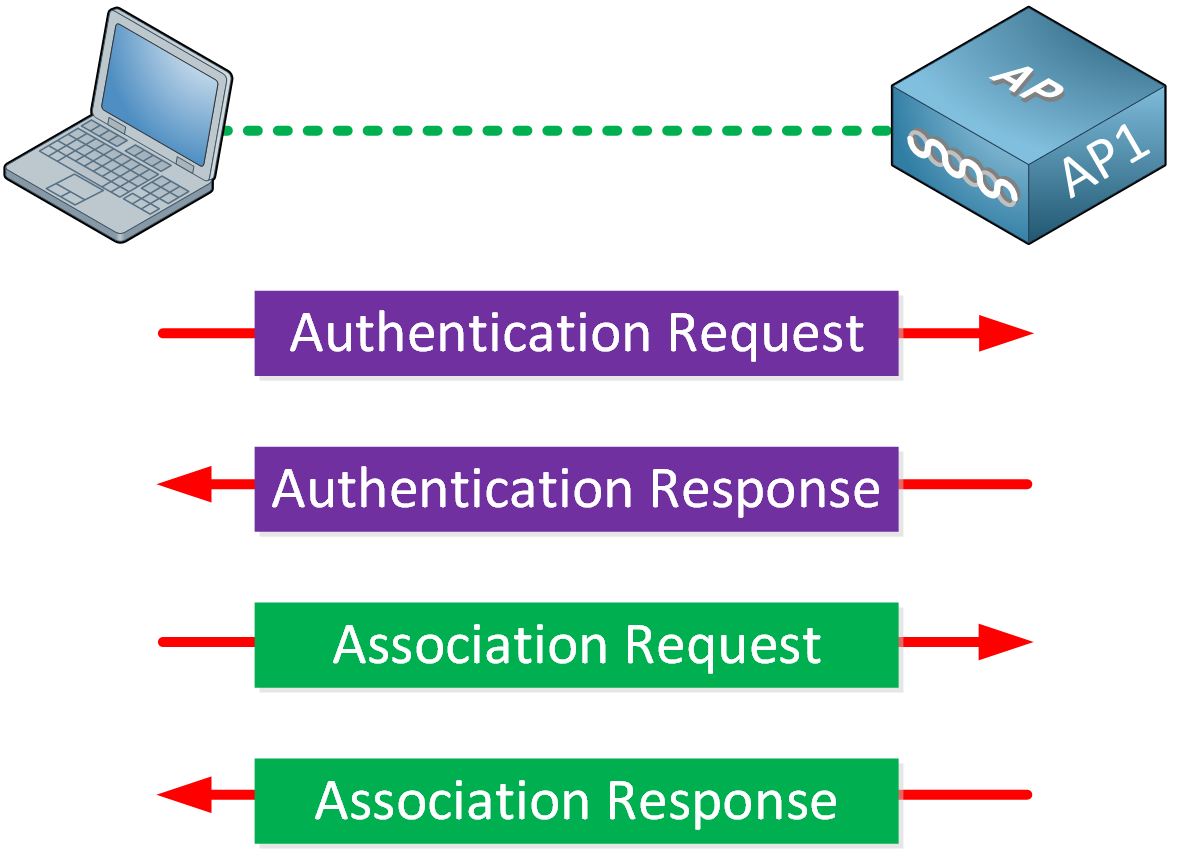
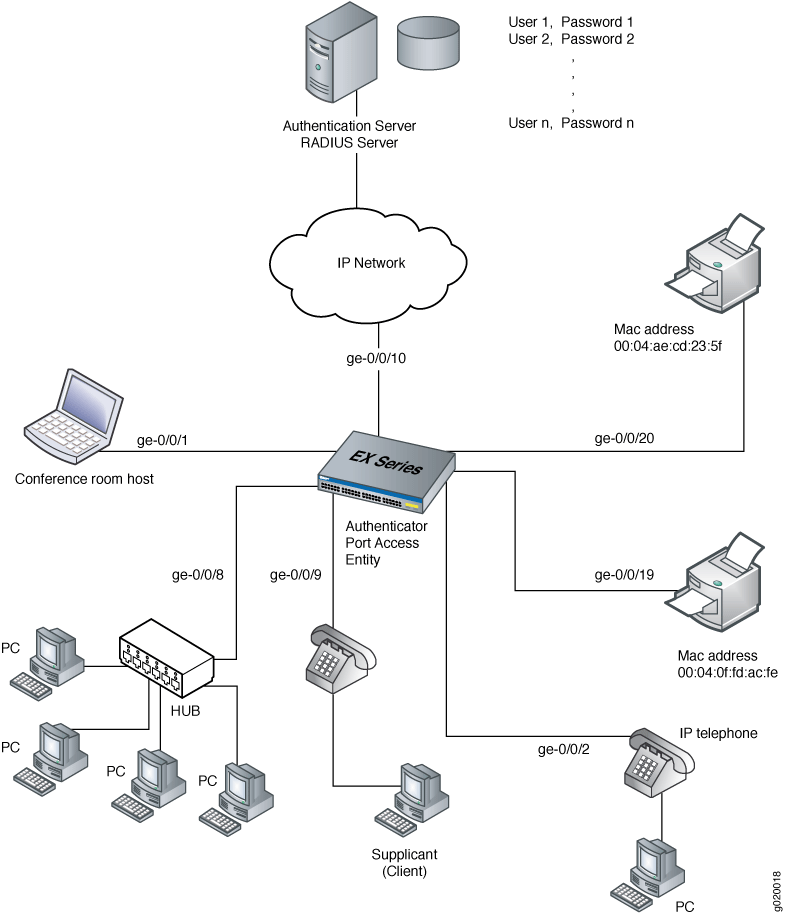
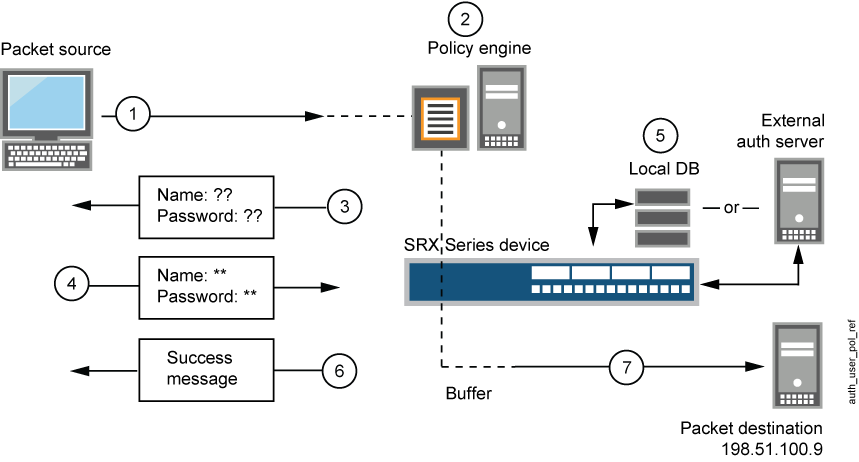
How to Configure Web Authentication (Local Authentication Server & Local Web Server) on TP-Link CAP/AC Serial Products

Linksys Official Support - What are Authentication Types, Basic Rate and Transmission Rate and how to Enable or Disable them


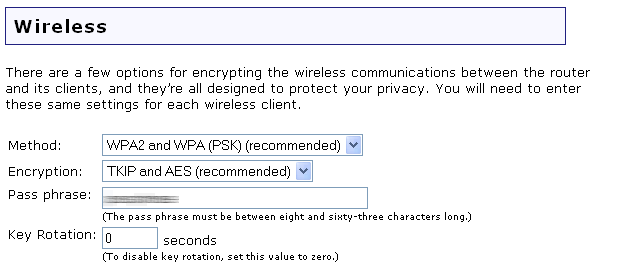
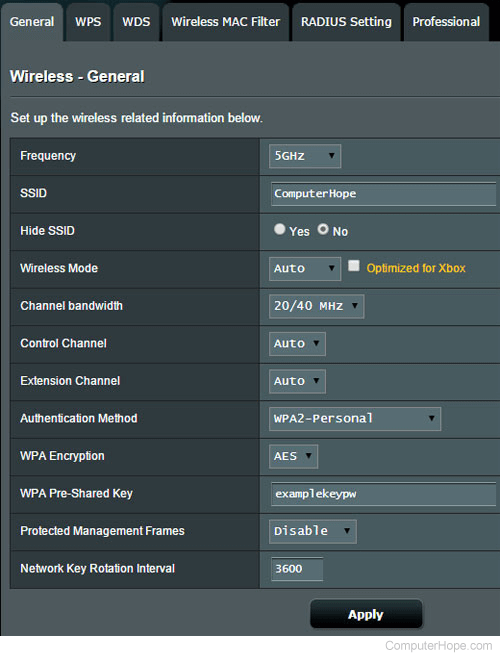
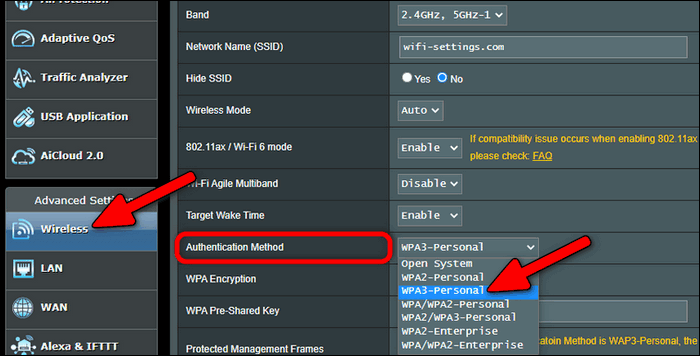
![Wireless] How to make my router more secure? | Official Support | ASUS Global Wireless] How to make my router more secure? | Official Support | ASUS Global](https://kmpic.asus.com/images/2019/03/20/f9a73fcd-639b-419f-87e6-200e1b665579.png)








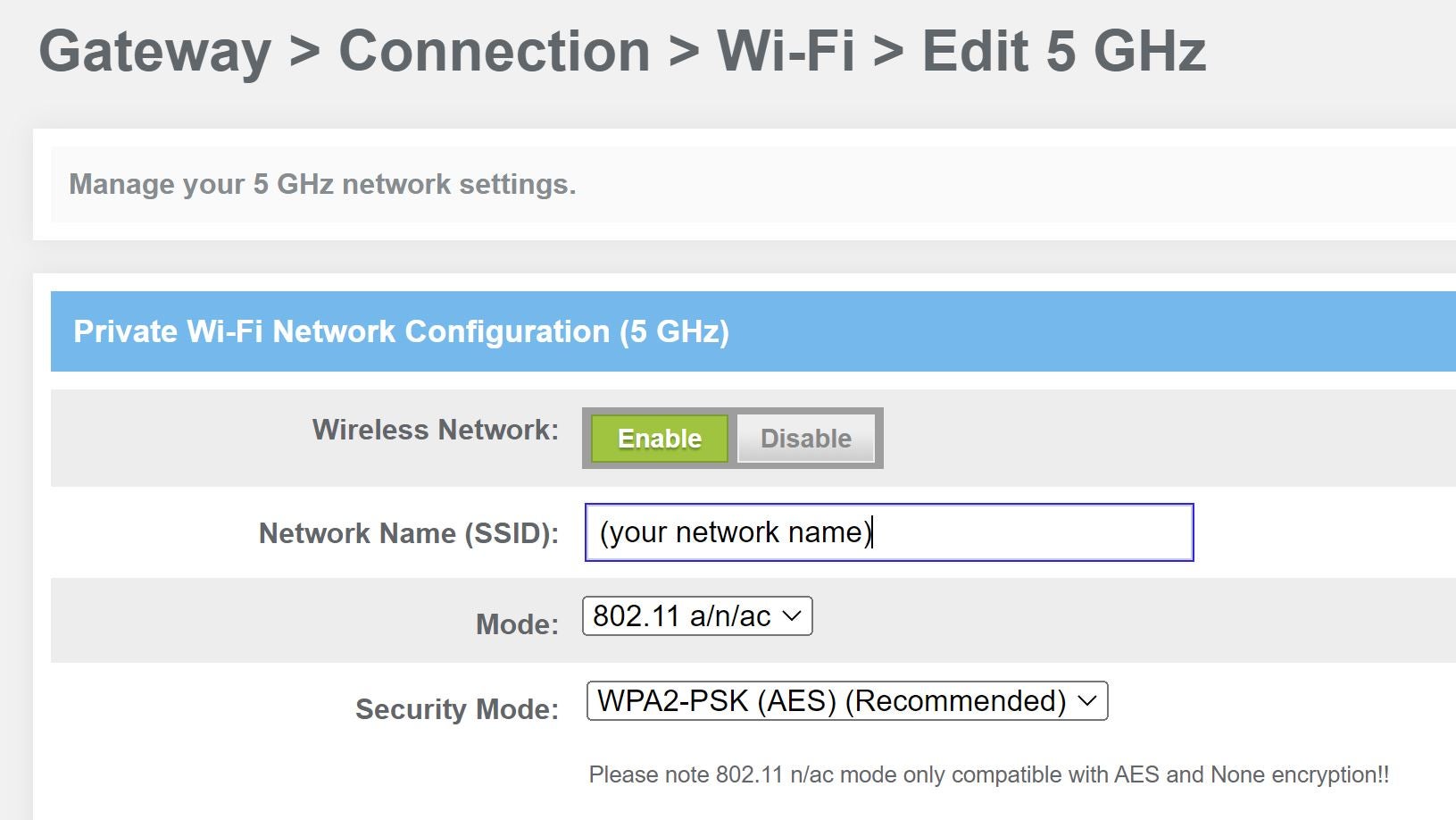
![Wireless] How to set up Guest Network? | Official Support | ASUS Global Wireless] How to set up Guest Network? | Official Support | ASUS Global](https://kmpic.asus.com/images/2020/03/19/6acf8489-d3ed-4c6b-a0a8-7ac4405d464a.jpg)